Weekly Zeitgeister: Middle Management Engineers its Own Demise, Infrastructure Abandoned, Patches Fail
Plus: 'The bot did it' won't hold up in court, 100K-star GitHub project becomes attacker magnet, and more — Powered by Zeitgeister.
What is Weekly Zeitgeister?
Weekly Zeitgeister is a new series powered by Zeitgeister, a tool I built to track what’s actually moving in tech, rank top stories, and turn them into usable insight. Each week, I pull one high-signal headline per day from Zeitgeister, attach a brief summary, and then share why it matters if you’re building or running software at scale.
This Week at a Glance
Monday’s Headline: Amazon Axes 16,000 Jobs While Doubling Down on AI: The Middle Manager Who Built His Own Guillotine
Tuesday’s Headline: Microsoft’s January Patch Tuesday Dumpster Fire: Boot Loops, Emergency Fixes, and the AI Chickens Coming Home to Roost
Wednesday’s Headline: Ingress NGINX's Burnout Crisis: 50% of K8s Clusters Face Unpatched Vulnerabilities After March 2026 Retirement
Thursday’s Headline: The AI Accountability Vacuum: When “The Bot Did It” Becomes Corporate America’s Favorite Excuse
Friday’s Headline: Moltbot’s Wild Ride: From 100K GitHub Stars to Infostealer Honeypot in Record Time
Monday – Amazon Axes 16,000 Jobs While Doubling Down on AI: The Middle Manager Who Built His Own Guillotine
Sentiment Analysis: 15% Positive | 25% Neutral | 60% Negative
What happened
Amazon announced 16,000 job cuts targeting middle management layers that AI systems are now automating—explicitly framed as “reducing layers” and “removing bureaucracy,” not pandemic overcorrection or belt-tightening.
One L7 manager reportedly built AI tools to replace his own function, automating information aggregation, reporting synthesis, and upward communication—the exact coordination work that justified middle management roles at scale.
The timing signals strategic intent, not cost pressure: Amazon is simultaneously investing heavily in AI infrastructure and data centers, revealing a bet that AI-enabled flat structures deliver competitive advantages traditional hierarchies cannot.
Why it matters
Organizational architecture risk: This isn’t “AI as productivity tool”—it’s AI replacing entire management layers that coordinate work and translate between strategy and execution.
Institutional knowledge evaporation: Middle managers hold critical context about systems, customers, and organizational history—AI cannot capture this, leading to repeated mistakes.
Consumer demand paradox: Eliminating jobs while depending on employed consumers creates systemic economic risk if this pattern spreads broadly.
Competitive pressure despite risks: With ASML and others making similar moves, companies may face strategic pressure to respond—even with execution risks and uncertain outcomes.
Actionable Insights
Audit management layers with brutal honesty: Map which functions are information aggregation versus strategic decision-making—the former are vulnerable, the latter remain human-critical.
Invest in augmentation, not replacement initially: Build tools that handle reporting while keeping humans in decision loops—reduce risk while building AI capability.
Redesign IC roles for greater ownership: If management layers shrink, ICs need more autonomy and decision-making—start the cultural shift now, not post-layoffs.
Develop sustainable growth beyond headcount reduction: Cost-cutting delivers one-time gains—tech leaders need strategies for how AI enables new revenue or market expansion.
Boardroom Talking Point
“Amazon’s 16,000 job cuts aren’t cost-cutting—they’re removing management layers that AI now handles. We need to audit which functions are coordination versus strategy and invest in augmentation before replacement, or we’ll face this same decision under market pressure rather than strategic choice.”
Tuesday – Microsoft’s January Patch Tuesday Dumpster Fire: Boot Loops, Emergency Fixes, and the AI Chickens Coming Home to Roost
Sentiment Analysis: 5% Positive | 15% Neutral | 80% Negative
What happened
Microsoft’s January 2026 Windows 11 security updates are causing widespread boot failures—this is the second emergency “out of band” patch within the same month, an unprecedented frequency signaling deeper systemic problems in development and testing.
The technical community attributes this to AI-driven development plus layoffs—AI-generated code lacking adequate human review combined with hollowed-out testing infrastructure creates a perfect storm where cost-cutting through AI efficiency undermines institutional knowledge.
Experienced users are abandoning Windows entirely for Linux and MacOS—migration is accelerating just as Microsoft pushes aggressive “agentic OS” features, eroding platform trust at the worst possible time.
Why it matters
Risk (velocity without verification): Microsoft’s second emergency patch in one month proves velocity without verification leads to catastrophic failure—this is the cautionary tale.
Cost (vendor trust breakdown): Microsoft’s crisis demonstrates even major vendors can’t be trusted for automatic updates—every organization now faces unplanned testing and rollback overhead.
People (knowledge loss): Nobody left to catch AI-typical errors like reimplemented libraries and missing edge cases when you cut the humans who understand complex systems.
Actionable Insights
Implement mandatory human review for AI-generated code immediately: Create processes specifically designed to catch AI-typical errors—logic drift, edge cases, reimplemented libraries, boot sequence vulnerabilities.
Maintain “theory of the software” ownership: Ensure senior engineers retain deep system architecture understanding even when using AI tools—don’t let AI become a black box.
Create controlled update environments now: Implement staged rollout processes for all critical systems—test on representative hardware before broad deployment, as Microsoft’s failure proves vendors can’t be trusted.
Boardroom Talking Point
“Microsoft shipped two emergency patches in one month because AI-driven development eliminated the senior engineers who catch kernel-level bugs. We’re implementing mandatory AI code review and staged rollouts—velocity without verification is what’s driving users to abandon Windows.”
Wednesday – Ingress NGINX's Burnout Crisis: 50% of K8s Clusters Face Unpatched Vulnerabilities After March 2026 Retirement
Sentiment Analysis: 15% Positive | 25% Neutral | 60% Negative
What happened
Kubernetes is retiring Ingress NGINX in March 2026 with no more security patches, bug fixes, or updates—affecting approximately 50% of cloud-native environments that built their entire ingress strategy around a tool maintained by 1-2 volunteers.
The maintainers finally burned out after years of warnings about unsustainable workload, exposing how widespread enterprise adoption occurred without corresponding contribution, funding, or support.
No drop-in replacement exists: Organizations face a forced migration with significant re-architecting required—Gateway API demands different patterns, while alternative controllers (F5 NGINX, Traefik, HAProxy, Envoy Gateway) each have limitations and learning curves.
Why it matters
Unpatched vulnerability exposure: Organizations that miss the March 2026 deadline will run ingress infrastructure with known security vulnerabilities and no patch path.
Hidden infrastructure dependencies: Many organizations may not know they’re using Ingress NGINX—discovering the problem only during exploits or audits in environments with poor documentation.
Broader open source fragility signal: If half the Kubernetes ecosystem can depend on unpaid volunteers until it breaks, what other critical infrastructure is similarly fragile?
Actionable Insights
Audit immediately using kubectl: Identify all clusters running Ingress NGINX—assume you’re affected until proven otherwise, and don’t rely on institutional knowledge given turnover rates.
Allocate dedicated migration resources now: This isn’t a background task—budget for dedicated team time and expect 2-4 months of work depending on environment complexity and testing requirements.
Evaluate Gateway API first, but have backup plan: Start with Gateway API migration using tools like ingress2gateway, but be ready to switch if gaps block critical functionality.
Conduct broader dependency audit: Use this crisis to identify other single-maintainer or under-resourced projects in your infrastructure before they reach similar breaking points.
Boardroom Talking Point
“Half of Kubernetes environments face forced infrastructure migration by March 2026 with no security patches afterward. Critical infrastructure maintained by 1-2 unpaid volunteers finally collapsed—we need systematic audits of all dependencies to identify similar risks before they become forced migrations under time pressure.”
Thursday – The AI Accountability Vacuum: When “The Bot Did It” Becomes Corporate America’s Favorite Excuse
Sentiment Analysis: 15% Positive | 25% Neutral | 60% Negative
What happened
A critical governance crisis is emerging around enterprise AI implementations—organizations are deploying AI agents with system access and autonomous decision-making authority without establishing clear accountability frameworks, creating a dangerous gap between technological capability and legal responsibility.
The “hallucination defense” is becoming the corporate scapegoat—when AI causes data breaches, compliance violations, or financial errors, companies blame the AI rather than taking responsibility, but courts and regulators won’t accept “the bot did it” as legitimate defense.
Organizations are rushing from ChatGPT queries to autonomous agents—moving from simple questions to systems with database access and autonomous execution without implementing the verification layers, approval workflows, or audit trails necessary to maintain accountability.
Why it matters
Legal liability (accountability void): When AI agents cause harm, determining responsibility becomes impossible without proper logging—the first major incident will establish enterprise liability regardless of claims.
Compliance risk (regulatory exposure): As AI governance frameworks emerge globally, organizations without clear accountability chains face retroactive compliance requirements and potential penalties.
Reputation (reckless deployment perception): Implementing AI agents without proper governance creates the appearance of reckless deployment—a single mistake can undermine years of trust-building.
Actionable Insights
Mandate human verification for all AI outputs before external use: Implement approval workflows where humans review AI-generated content—treat AI like an intern whose work must be checked.
Audit your permissions infrastructure before deploying AI tools: SharePoint Copilot shows AI can respect security boundaries, but only if properly configured—conduct permissions audits focused on AI system access.
Establish “canonical metrics” for business-critical queries now: For recurring questions like revenue or customer counts, create human-verified query templates that eliminate probabilistic risk.
Implement comprehensive prompt and output logging immediately: Maintain your own audit trail of prompts, permissions, AI outputs, and approvals—this is your legal defense when things go wrong.
Boardroom Talking Point
“AI accountability is becoming a legal liability issue—organizations are deploying systems where it’s genuinely unclear who is responsible when the AI makes mistakes. The ‘hallucination defense’ won’t work in court. We’re implementing human verification workflows, permissions audits, and comprehensive logging before expanding AI agent deployments.”
Friday – Moltbot's Wild Ride: From 100K GitHub Stars to Infostealer Honeypot in Record Time
Sentiment Analysis: 25% Positive | 20% Neutral | 55% Negative
What happened
OpenClaw (formerly Moltbot) exploded to 100,000+ GitHub stars by promising autonomous AI assistance—it can manage email, calendars, files, and code repositories, and attackers added it to their target lists within days after RedLine, Lumma, and Vidar infostealers began exploiting it.
The security architecture is fundamentally broken by design—no mandatory authentication, exposed API endpoints, prompt injection vulnerabilities, and shell access granted by default, yet developers are connecting it to their most sensitive systems.
Researchers extracted SSH private keys via email prompt injection in five minutes—hundreds of instances are exposing API keys, OAuth tokens, and months of private conversations to the public internet, with one firm reporting nearly 8,000 attack attempts.
Why it matters
Security (autonomous agent risk): This is the first widely-deployed autonomous agent with enough real-world access to matter—it’s a preview of the AI agent security crisis to come.
Risk (shadow IT): Developers are deploying without IT approval, and the project’s rapid rebranding makes detection harder for security teams tracking unauthorized deployments.
Cost (API burn rate): Multiple users reported burning through hundreds of dollars in API costs within days—one user spent $560 in a weekend.
Actionable Insights
Audit your environment immediately for OpenClaw/Moltbot/Clawdbot instances: Scan for port 18789 exposure, check cloud billing for related API usage, and search internal channels—developers are deploying without approval.
Establish AI agent governance before permitting autonomous deployments: Create clear policies on what systems AI agents can access with mandatory security controls and approval processes.
Implement “least privilege” architecture for any AI agent: Create dedicated accounts with limited permissions—assume the agent will be compromised and design accordingly.
Boardroom Talking Point
“We’re seeing AI agents deployed without IT approval and immediately targeted by commodity infostealers. We’re auditing for unauthorized instances and implementing mandatory governance before any autonomous AI system touches production data.”
There you have it: five days, five headlines - each with a breakdown of what happened, why it matters for tech leaders, what to do next, and what to say to show stakeholders you’re aware and prepared for the future.
Back with another Weekly Zeitgeister next week.
Enjoy your weekend!
Bobby
P.S. If you’d rather see trends personalized to you - mapped, explained, and ranked to your domains, your vendors, and your board conversations - do give Zeitgeister a try.
It’s free, and you’ll get:
🧠 Agnostic trend feed across Reddit, HN, news, and more
📊 Synthesized briefings with context, risks, and opportunities
🗣️ Stakeholder-ready talking points for CEOs, boards, and PE partners
⏱️ Saves me a couple of hours a week on “what’s going on and why do I care?”




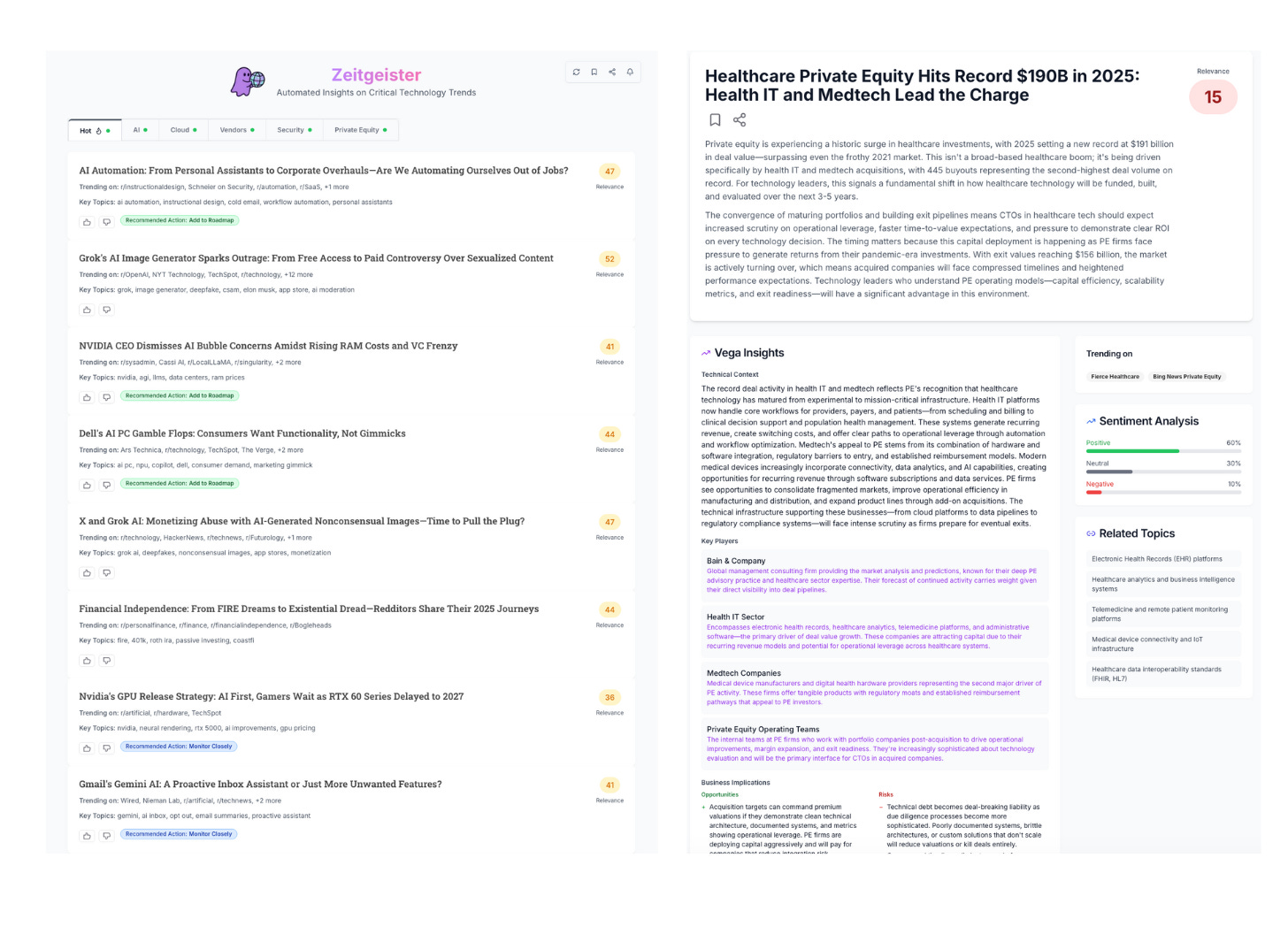
The Amazon AI job cuts really got me thinking. What if this trend accelerates, leading to mass displacment without new AI-driven rols emerging fast enough? I wonder.